videoOVerview on prevention of AIDSGo through AIDS definition by WHO
- Subject:
- Health, Medicine and Nursing
- Material Type:
- Module
- Author:
- kirti jamdar
- Date Added:
- 08/09/2017

videoOVerview on prevention of AIDSGo through AIDS definition by WHO

Description: Students play with an AI that can react to their movement, and choreograph something that uses this tool. They can show off their choreography to the rest of the class
Skills/knowledge you'll gain: Movement, collaboration
Length: 1-4 hours
Curriculum aligns to:
- NGSS Engineering standards
- ISTE standards
- Common Core ELA/Literacy standards
- Also maps to CSTA standards

Description: AI can create realistic-looking images and videos that were never actually filmed or taken as a photo. These images and videos are called deepfakes. This is a quick lesson requiring no background where students learn about deepfakes, as well as ways to verify information that they see
Skills/knowledge you'll gain: Critical thinking
Length: 1 hour
Curriculum aligns to:
- NGSS Engineering standards
- ISTE standards
- Common Core ELA/Literacy standards
- Also maps to CSTA standards

Description: A quick and fun way to become familiar with some core ideas of modern AI while playing with Google Quick, Draw
Skills/knowledge you'll gain: Understanding of what AI is, privacy and bias concerns
Length: 1 hour
Curriculum aligns to:
- NGSS Engineering standards
- ISTE standards
- Common Core ELA/Literacy standards
- Also maps to CSTA standards

Description: An interactive deep dive into the sort of ethical concerns that companies creating AI based systems should consider. Students explore these ideas through role-playing running their own companies and making ethical decisions for those companies
Skills/knowledge you'll gain: Human-centered design, ethics
Length: 10 hours
Curriculum aligns to:
- NGSS Engineering standards
- ISTE standards
- Common Core ELA/Literacy standards
- Also maps to CSTA standards

Description: A short deep dive into how facial recognition technology is used, some biases it has, and some ways companies, individuals, and the law are fighting against its use in surveillance
Skills/knowledge you'll gain: Ethics
Length: 1 hour
Curriculum aligns to:
- NGSS Engineering standards
- ISTE standards
- Common Core ELA/Literacy standards
- Also maps to CSTA standards

This resource includes traditional writing prompts as well as prompts and assignments that utilize AI-generated text. It covers the fields of Creative Writing, Composition, and Business and Technical Writing.

Description: Learn how conservationists use AI image recognition to save time identifying how and where to protect endangered species. Build your own species-identifying AI system
Skills/knowledge you'll gain: Conservation
Length: 1-2 hours
Curriculum aligns to:
- NGSS Engineering standards
- ISTE standards
- Common Core ELA/Literacy standards
- Also maps to CSTA standards

This assignment is about exploring alternative ways of sharing goods and services and understanding the benefits, drawbacks, and implications of these methods. Students are asked to choose one of seven non-market distribution methods, such as majority rule, contests, force, first-come/first-served, sharing equally, lottery, and personal characteristics, and observe how it is implemented in real-life scenarios. They need to explain the distribution method, who benefits from it, who is excluded, and the advantages and disadvantages of using it. Students also have to find a real-life example of the chosen non-market distribution method, describe how it is used, and assess its fairness and efficiency. Lastly, they are required to include a citation and ensure their submission is no less than 180 words and comprises a list of cited works. The goal of the assignment is to better understand how goods and services are distributed and how these methods affect different groups of people.

Couture pattern-making and sewing techniquesAmsterdam Fashion InstituteFashion & DesignYear 2Semester 4

Basic pattern-making and sewing techniquesAmsterdam Fashion InstituteFashion & DesignYear 2Semester 4

Basic pattern-making and sewingAmsterdam Fashion InstituteFashion & DesignYear 2Semester 3

In this class, we will explore America's diversity through questions of immigration, race, gender/sexuality and class--some of the major ways our culture is organized. It is comprised of 9 lessons based on online resources, plus 2 auto-ethnography assignments. This class was originally taught by Huma Mohibullah at Renton Technical College.

Religion is a significant aspect of human cultures everywhere. In these lessons, we explore questions such as: What are the main elements of religion? Why is believing in a higher power important to human beings across cultures? How is religion related to our social orders? How is religion related to the politics of today's world?This resource is comprised of 7 lessons based on online modules, plus a final presentation assignment. Each lesson includes a discussion or written assignment. This class was originally taught by Huma Mohibullah at Renton Technical College.

Sa modyul na ito, inaasahang matutuhan ang mga sumusunod:
1. Nasusuri ang pag-unlad at pag-usbong ng mga klasikong lipunan sa Africa
at mga pulo sa Pasipiko.

A strong foundation in science (including this social science) has always been an essential element of post-secondary education. The current White House administration demonstrates that people are much more impressionable when they don't have the critical tools to question so-called experts. Critical analysis of research has always been integral to the sciences, but with so much misinformation coming out of those in power, it is more important than ever to have a strong background in science and research.
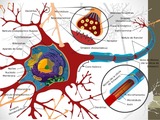
Anatomy and Physiology Lab I slide decks created by Steven Lee M.S. Pathology, FTCC. The PowerPoints include labeled body images to assist students in identifying body parts. Nicole Shaw is only responsible for assisting Steven with licensing his work under an open license and uploading content to the Commons.
In the last two decades, research in various aspects of mobile ad-hoc networks, MANETs, has been very active, motivated mainly by military, disaster relief and law enforcement scenarios. More recently, location information has become increasingly available; partially prompted by the emerging trend to incorporate location or position sensing into personal handheld devices. An evolutionary natural step is to adopt such position-based operation in MANETs. This results in what we call position-based MANETs. In such settings, devices are equipped with position-sensing capabilities and rely on position information in their operation. The main distinguishing feature of the envisaged position-based MANET environment is the communication paradigm based not on permanent or semi-permanent identities, addresses or pseudonyms, but on instantaneous node locations or positions. In some application settings, such as: military, law enforcement and search-and-rescue, node identities are not nearly as important as node positions. Such settings have certain characteristics in common. First, node position is very important: knowledge of the physical, as opposed to logical or relative topology, makes it possible to avoid wasteful communication and focus on nodes located within a specific area. Thus, the emphasis is not on the longterm node identity, but rather on current node position. Second, critical environments face security and privacy attacks. Security attacks aim to distribute false location and network ing control information, e.g., routing control messages, or impede the propagation of genuine information. The goal of privacy attacks is to track nodes as they move. Third, when the operating environment is hostile, as is the case in military and law enforcement settings, node identities must not be revealed. We use the term hostile to mean that communication is being monitored by adversarial entities that are not part of the MANET. The need to hide node identities becomes more pressing if we further assume that MANET nodes do not trust each other, due to a suspicious environment where nodes can be compromised. In such an environment, it is natural for node movements to be obscured, such that tracking a given node is impossible or, at least, very difficult. While we do not claim that such suspicious and hostile location-based MANET environments are commonplace, they do occur and require high security and privacy guarantees. While doing all these;there is a challenge for nodes to maintain anonymity protection from outside observers or malicious attackers. Full anonymity protection can be achieved only when ;sources,destinations and routes all are protected. In this work, to offer better anonymity protection, we propose an Anonymous Position-based Security Aware Routing Protocol (APSAR). Experimental results exhibit consistency with the theoretical analysis, and show that APSAR achieves better route anonymity protection compared to other anonymous routing protocols. Also, APSAR achieves comparable routing efficiency to the GPSR geographical routing protocol. The work in this thesis addresses a number of security and privacy issues arising in position-based MANETs. models. We address the problem of position based security aware routing in consideration with better anonymity protection .

The Open for Antiracism (OFAR) Program – co-led by CCCOER and College of the Canyons – emerged as a response to the growing awareness of structural racism in our educational systems and the realization that adoption of open educational resources (OER) and open pedagogy could be transformative at institutions seeking to improve. The program is designed to give participants a workshop experience where they can better understand anti-racist teaching and how the use of OER and open pedagogy can empower them to involve students in the co-creation of an anti-racist classroom. The capstone project involves developing an action plan for incorporating OER and open pedagogy into a course being taught in the spring semester. OFAR participants are invited to remix this template to design and share their projects and plans for moving this work forward.
In this module we will provide a comprehensive description of the legal landscape of the assistive technology locally and on an international level as well as best practices.